

一种用于DEM数据认证与篡改定位的感知哈希算法
|
张鑫港(1997— ),男,山东济宁人,硕士生,主要从事空间数据安全的研究。E-mail:1441861764@qq.com |
收稿日期: 2019-06-26
要求修回日期: 2019-12-29
网络出版日期: 2020-05-18
基金资助
国家自然科学基金项目(71563025)
国家自然科学基金项目(41761080)
甘肃省高等学校产业支撑引导项目(2019C-04)
兰州交通大学优秀平台支持项目(201806)
版权
A Perceptual Hash Algorithm for DEM Data Authentication and Tamper Localization
Received date: 2019-06-26
Request revised date: 2019-12-29
Online published: 2020-05-18
Supported by
National Natural Science Foundation of China(71563025)
National Natural Science Foundation of China(41761080)
Industrial Support and Guidance Projects of Colleges and Universities in Gansu Province(2019C-04)
Funded by Lanzhou Jiaotong University Excellent Platform(201806)
Copyright
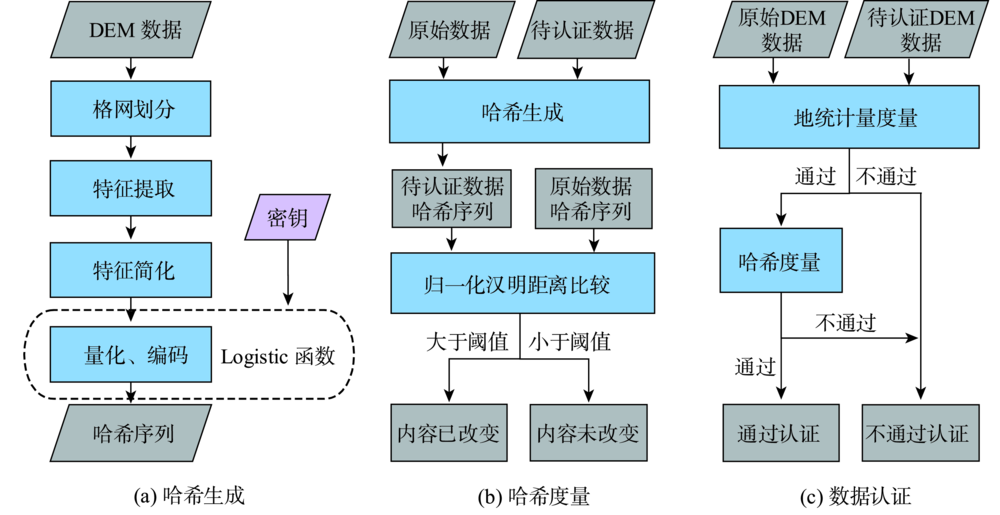
DEM数据作为重要的基础地理信息数据,其数据完整性问题不容忽视。基于DEM数据完整性认证的要求,以及相关认证算法的欠缺,本文运用感知哈希技术设计了一种DEM数据认证算法,并可实现篡改定位。因DEM数据具有数据量大、细节丰富的特点,首先对其进行规则格网划分,将其划分为互不重叠的格网单元;然后对格网单元数据进行DCT分解,提取数据的特征信息以生成特征向量矩阵,并对特征向量矩阵进行摘要化处理;随后,使用Logistic混沌系统对简化后的特征向量矩阵进行置乱;对置乱矩阵进行量化、编码后,便可生成感知哈希序列。在数据认证时,首先计算原始数据与待验证数据的高程相对中误差,再将二者的感知哈希序列进行归一化汉明距离度量,结合判定阈值,即可对DEM数据进行数据认证与篡改定位。该算法对DEM数据的格式转换、水印嵌入等攻击有较强的鲁棒性,对各类改变内容的操作具有敏感性,并可实现DEM数据微小篡改的识别与定位。与已有的DEM完整性认证方法相比,将DEM数据的“内容”作为完整性度量的重要标准,在具体应用中更具有实用价值。
张鑫港 , 闫浩文 , 张黎明 . 一种用于DEM数据认证与篡改定位的感知哈希算法[J]. 地球信息科学学报, 2020 , 22(3) : 379 -388 . DOI: 10.12082/dqxxkx.2020.190336
As a type of fundamental and important geographic data, the integrity of DEM data cannot be ignored. The commonly used technology for data integrity authentication is mainly based on traditional cryptography and digital watermarking technology. The former is very sensitive to the change of every bit of data, suitable for accurate authentication of text data; while latter is mostly based on data carrier for authentication, seldom considers if DEM data content changes or not, and needs additional secure channels and communication media. In this paper, based on the requirement of authenticity and integrity of DEM data and the shortcomings of related authentication algorithms, a DEM data authentication algorithm was designed based on the Perceptual Hashing technology, which can achieve tamper localization. Perceptual hashing is a kind of method that maps multimedia data unidirectionally into perceptual summary sets (i.e. hash sequences). It inherits the characteristics of traditional Hash functions such as unidirectionality, anti-collision, and summarization, and is robust to the operation of content preservation, so it can better meet the requirements of DEM data authentication. The main ideas of this algorithm are as follows: Based on the characteristics of a large amount of DEM data and abundant details, the DEM data is divided into regular and non-overlapping grids. Feature extraction is the key of Perceptual Hashing algorithm. In this paper, the discrete cosine transform was used to extract features and generate the eigenvector matrix. Then the eigenvector matrix was digested. Next, the simplified eigenvector matrix was scrambled by using a Logistic chaotic system to meet the security requirements of authentication. Followingly, the scrambled matrix was quantized and coded to generate perceptual hash sequence. In the data authentication stage, the relative error of elevation between the original data and the data to be validated was calculated firstly. Subsequently, the perceptual hash sequence of the original data and the data to be validated was normalized to measure the Hamming distance. Combined with the determination threshold, the DEM data was authenticated. The scope of tampering would be located on the "grid unit" mentioned above. The algorithm has strong robustness against DEM data format conversion, watermarking embedding and other attacks. It is sensitive to various operations of changing contents, and can recognize and locate minor tampering of DEM data. Compared with the traditional DEM authentication algorithm, this algorithm innovatively regards "content" as the sole criterion of identity determination, which effectively compensates for the traditional digital watermarking method's excessive dependence on information carriers.

表1 鲁棒性测试统计结果Tab. 1 Statistical results of robustness tests |
| 攻击类型 | 数据A | 数据B | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 相对中误差检测 | 哈希度量 | 认证结果 | 准确性 | 相对中误差检测 | 哈希度量 | 认证结果 | 准确性 | ||
| 水印嵌入 | 通过 | 通过 | 通过认证 | 准确 | 通过 | 通过 | 通过认证 | 准确 | |
| 格式转为img | 通过 | 通过 | 通过认证 | 准确 | 通过 | 通过 | 通过认证 | 准确 | |
| 格式转为dat | 通过 | 通过 | 通过认证 | 准确 | 通过 | 通过 | 通过认证 | 准确 | |
表2 篡改检测统计结果Tab. 2 Statistical results of tamper detection |
| 攻击类型 | 数据A | 数据B | |||||||
|---|---|---|---|---|---|---|---|---|---|
| 中误差检测 | 哈希度量 | 认证结果 | 准确性 | 中误差检测 | 哈希度量 | 认证结果 | 准确性 | ||
| 不做修改 | 通过 | 通过 | 通过 | 准确 | 通过 | 通过 | 通过 | 准确 | |
| 高程平移(10 m) | 不通过 | — | 不通过 | 准确 | 不通过 | — | 不通过 | 准确 | |
| 高程缩放(99%) | 不通过 | — | 不通过 | 准确 | 不通过 | — | 不通过 | 准确 | |
| 噪声攻击(0.1%) | 通过 | 不通过 | 不通过 | 准确 | 不通过 | — | 不通过 | 准确 | |
| 噪声攻击(1%) | 不通过 | — | 不通过 | 准确 | 不通过 | — | 不通过 | 准确 | |
| 众值滤波(4像元) | 通过 | 不通过 | 不通过 | 准确 | 通过 | 不通过 | 不通过 | 准确 | |
| 众值滤波(8像元) | 通过 | 不通过 | 不通过 | 准确 | 通过 | 不通过 | 不通过 | 准确 | |
| 部分替换 | 不通过 | — | 不通过 | 准确 | 不通过 | — | 不通过 | 准确 | |
表3 汉明距离统计结果Tab. 3 Statistical results of the Hamming distance |
| 数据名称 | 格网类型 | 平均汉明距离 |
|---|---|---|
| A' | 篡改格网 | 0.836 |
| 未篡改格网 | 0.010 | |
| B' | 篡改格网 | 0.854 |
| 未篡改格网 | 0.009 |
| [1] |
汤国安 . 我国数字高程模型与数字地形分析研究进展[J]. 地理学报, 2014,69(9):1305-1325.
[
|
| [2] |
程春泉, 黄国满, 杨杰 . POS与DEM辅助机载SAR多普勒参数估计[J]. 测绘学报, 2015,44(5):510-517.
[
|
| [3] |
冯增文 . 基于多期DEM的地质灾害与环境动态监测[D]. 北京:中国地质大学(北京), 2015.
[
|
| [4] |
王雪, 李精忠, 余斌 . 基于DEM提取流域特征影响因子的分析[J]. 测绘与空间地理信息, 2019,42(6):38-42.
[
|
| [5] |
陈冬花, 邹陈, 王苏颖 等. 基于DEM的伊犁河谷气温空间插值研究[J]. 光谱学与光谱分析, 2011,31(7):1925-1929.
[
|
| [6] |
黄琪 . 基于DEM与LP的土地平整工程设计优化研究[D]. 南京:南京农业大学, 2011.
[
|
| [7] |
葛韬 . 某区域虚拟战场环境参谋系统的设计[D]. 大连:大连理工大学, 2017.
[
|
| [8] |
丁勇 . 密码学与信息安全简明教程[M]. 北京: 电子工业出版社, 2015.
[
|
| [9] |
辛运帏, 廖大春, 卢桂章 . 单向散列函数的原理、实现和在密码学中的应用[J]. 计算机应用研究, 2002,19(2):25-27.
[
|
| [10] |
朱长青, 杨成松, 任娜 . 论数字水印技术在地理空间数据安全中的应用[J]. 测绘通报, 2010(10):1-3.
[
|
| [11] |
|
| [12] |
许惠 . 基于数字水印技术的地理数据篡改责任认定方法研究——以DEM数据为例[D]. 南京:南京师范大学, 2015.
[
|
| [13] |
王刚, 任娜, 朱长青, 景旻 . 倾斜摄影三维模型数字水印算法[J]. 地球信息科学学报, 2018,20(6):738-743.
[
|
| [14] |
魏征, 闫浩文, 张黎明 . 抗高程平移和裁剪的格网DEM盲水印算法[J]. 测绘科学, 2016,41(8):170-173.
[
|
| [15] |
刘爱利, 丁浒, 田丹 , 等. 基于坡度和坡向分析的DCT域DEM数字水印算法[J]. 武汉大学学报·信息科学版, 2016,41(7):903-910.
[
|
| [16] |
朱长青, 许惠, 任娜 . 顾及地形特征的DEM脆弱水印完整性认证算法[J]. 地球信息科学学报, 2016,18(3):369-375.
[
|
| [17] |
|
| [18] |
牛夏牧, 焦玉华 . 感知哈希综述[J]. 电子学报, 2008,36(7):1405-1411.
[
|
| [19] |
|
| [20] |
|
| [21] |
张春艳, 李京兵, 王双双 . 基于离散小波变换和感知哈希的加密医学图像检索算法[J]. 计算机应用, 2018,38(2):539-544.
[
|
| [22] |
|
| [23] |
|
| [24] |
南希, 李爱农, 景金城 . 中国山地起伏度计算中地形自适应滑动窗口获取与验证[J]. 地理与地理信息科学, 2017,33(4):34-39.
[
|
| [25] |
陈艳丽, 李少梅, 刘岱岳 . 基于规则格网DEM的坡度坡向分析研究[J]. 测绘与空间地理信息, 2009,32(5):36-39.
[
|
| [26] |
王银堂, 李伶杰, 胡庆芳 等. 考虑局部趋势的非一致性水文频率分析方法[J]. 水科学进展, 2017,28(3):406-414.
[
|
| [28] |
晋蓓, 刘学军, 王彦芳 . 格网DEM坡度计算模型的相似性研究[J]. 测绘科学, 2009,34(6):131-134.
[
|
| [29] |
李赵红, 侯建军 . 基于Logistic混沌映射的DCT域脆弱数字水印算法[J]. 电子学报, 2006,34(12):2134-2137.
[
|
| [30] |
武汉大学测绘学院测量平差学科组. 误差理论与测量平差基础[M]. 武汉: 武汉大学出版社, 2009.
[ Subject Group of Surveying Adjustment, School of Surveying and Mapping, Wuhan University. The base of errors theory & surveying adjustment[M]. Wuhan: Wuhan University Press, 2009. ]
|
| [31] |
国家测绘局. 中华人民共和国测绘行业标准(基础地理信息数字产品1:10 000、1:50 000数字高程模型)[Z]. 2001.
[ State Bureau of Surveying and Mapping. Standards for surveying and mapping industry of the People's Republic of China (basic geographic information digital products 1:10 000, 1:50 000 DEM)[Z]. 2001. ]
|
| [32] |
|
/
| 〈 |
|
〉 |