

基于地图匹配和两阶段聚类的轨迹异常检测算法
作者贡献:Author Contributions
王书敏和俞庆英参与实验设计;王书敏完成实验操作;王书敏、李元俊、杨涛、俞庆英参与论文的写作与修改。所有作者均阅读并同意最终稿件的提交。
The study was designed by WANG Shumin and YU Qingying. The experimental operation was completed by WANG Shumin. The manuscript was drafted and revised by WANG Shumin, LI Yuanjun, YANG Tao, and YU Qingying. All the authors have read the last version of paper and consented for submission.
|
王书敏(1999— ),女,安徽滁州人,硕士生,主要从事空间数据处理研究。E-mail: 2221022481@ahnu.edu.cn |
收稿日期: 2025-03-24
修回日期: 2025-05-21
网络出版日期: 2025-07-23
基金资助
国家自然科学基金项目(62472006)
安徽省自然科学基金项目(2208085MF164)
A Trajectory Anomaly Detection Algorithm Based on Map Matching and Two-Stage Clustering
Received date: 2025-03-24
Revised date: 2025-05-21
Online published: 2025-07-23
Supported by
National Natural Science Foundation of China(62472006)
Anhui Provincial Natural Science Foundation of China(2208085MF164)
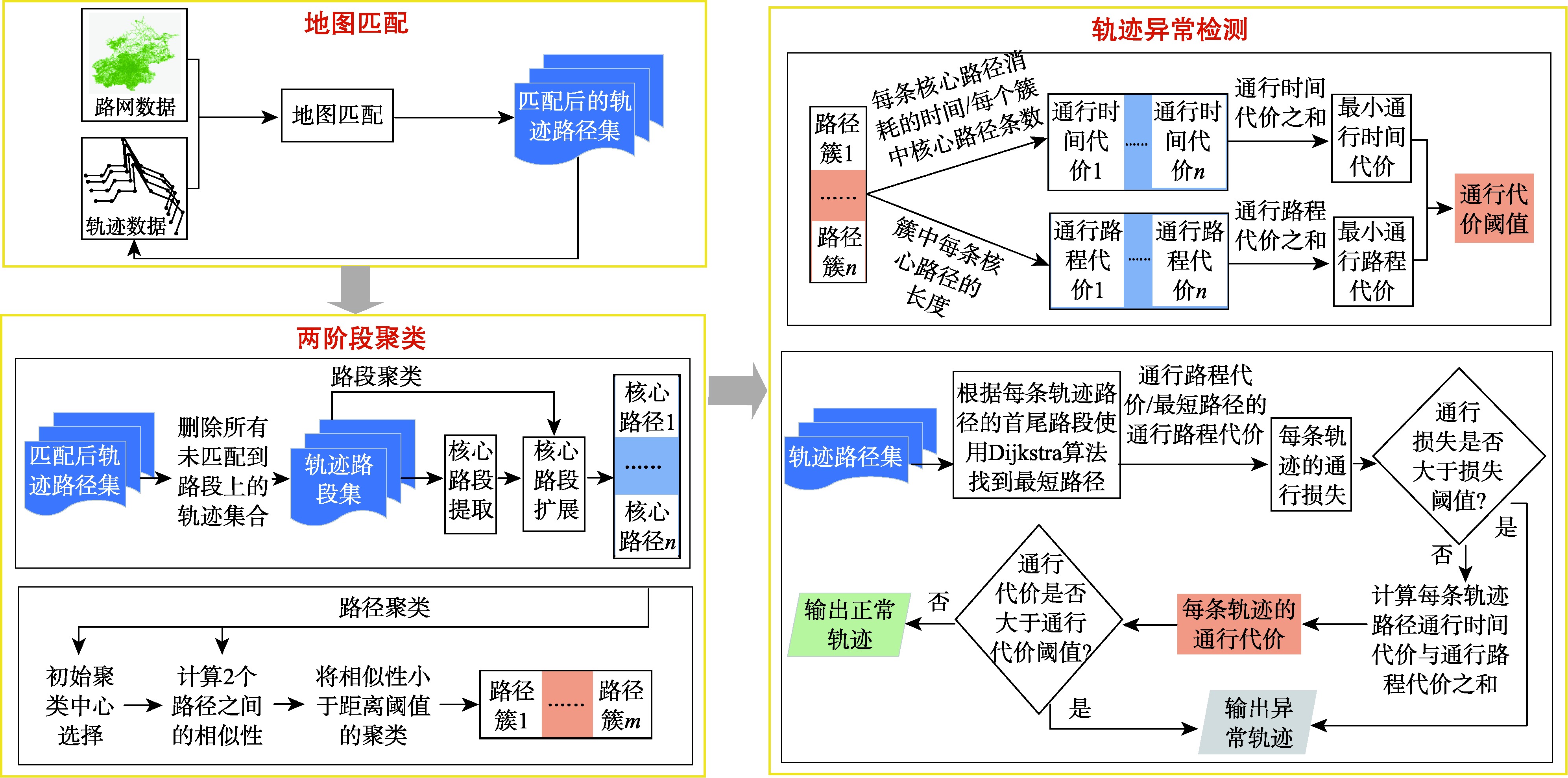
【目的】针对现有轨迹异常检测方法未充分考虑道路网络约束的问题,提出一种有效检测出租车司机搭载乘客时可能存在的欺诈行为的轨迹异常检测算法。【方法】首先进行地图匹配,将轨迹数据映射到实际道路网络上,从而获取轨迹的路径序列。接着,使用两阶段聚类方法,先对匹配后的轨迹路径进行初始聚类,提取出核心路段并扩展,形成多个核心路径,再计算不同核心路径之间的相似性,并将相似性高的路径分配到同一簇,从而形成多个路径簇。最后,根据路径簇计算出通行代价阈值,再结合通行时间代价和通行路程代价计算每条轨迹的通行代价,将其与通行代价阈值进行比较,以此判断轨迹的异常性。【结果】在真实轨迹数据集上与传统异常检测方法进行对比,所提方法在异常轨迹检测上具有良好的效果,其运行时间明显低于STADCS方法,并且检测准确率比STADCS方法最高提升了9.03%; F1分数值相较于Two Phase和ATDC方法也有明显提升,最高提升率分别为6.67%和9.45%。【结论】本文提出融合路网约束的检测方法,结合两阶段聚类和通行代价评估,有效提升检测准确性与效率,降低误判率。算法适用于复杂城市路网场景,为车辆轨迹数据挖掘及交通管理决策提供有力支持,在欺诈识别等领域具有重要应用价值。
王书敏 , 李元俊 , 杨涛 , 俞庆英 . 基于地图匹配和两阶段聚类的轨迹异常检测算法[J]. 地球信息科学学报, 2025 , 27(8) : 1780 -1795 . DOI: 10.12082/dqxxkx.2025.250134
[Objectives] To address the limitation that existing trajectory anomaly detection methods often fail to fully consider road network constraints, this study proposes a trajectory anomaly detection algorithm designed to effectively identify potential fraudulent behavior by taxi drivers during passenger pickup. [Methods] The algorithm first performs map matching, aligning trajectory data with the actual road network to obtain a sequence of path segments. Then, a two-stage clustering approach is applied: the matched trajectory paths are initially clustered to extract and expand core road segments, forming multiple core paths. Next, the algorithm calculates the similarity between different core paths and assigns highly similar paths to the same cluster, thereby generating multiple path clusters. Finally, a CostThreshold is computed based on each path cluster. The travel cost of each trajectory, calculated by combining travel time and distance costs, is compared against the corresponding CostThreshold to determine whether the trajectory is anomalous. [Results] Compared with traditional anomaly detection methods on real-world trajectory datasets, the proposed approach demonstrates superior performance in detecting anomalous trajectories. It achieves significantly lower runtime and improves detection accuracy by up to 9.03% compared to the STADCS method. The F1 score also improves considerably compared to the Two-Phase and ATDC methods, with maximum gains of 6.67% and 9.45%, respectively. [Conclusions] This paper presents a detection method that integrates road network constraints with two-stage clustering and travel cost evaluation. The method enhances detection accuracy and efficiency while reducing the false positive rate. It is well-suited for complex urban road networks, offering valuable support for vehicle trajectory data mining and traffic management decision-making, with significant practical value in fraud detection and related fields.

利益冲突:Conflicts of Interest 所有作者声明不存在利益冲突。
All authors disclose no relevant conflicts of interest.
| [1] |
曹翰林, 唐海娜, 王飞, 等. 轨迹表示学习技术研究进展[J]. 软件学报, 2021, 32(5):1461-1479.
[
|
| [2] |
|
| [3] |
|
| [4] |
廖祝华, 张健, 刘毅志, 等. 基于稀疏轨迹数据的出租车载客区域推荐[J]. 电子学报, 2020, 48(11):2178-2185.
[
|
| [5] |
|
| [6] |
|
| [7] |
|
| [8] |
|
| [9] |
|
| [10] |
Preeti,
|
| [11] |
|
| [12] |
李超能, 冯冠文, 姚航, 等. 轨迹异常检测研究综述[J]. 软件学报, 2024, 35(2):927-974.
[
|
| [13] |
|
| [14] |
|
| [15] |
|
| [16] |
|
| [17] |
|
| [18] |
|
| [19] |
|
| [20] |
|
| [21] |
|
| [22] |
|
| [23] |
|
| [24] |
|
| [25] |
|
| [26] |
|
| [27] |
|
| [28] |
|
| [29] |
|
| [30] |
|
| [31] |
|
| [32] |
|
| [33] |
|
/
| 〈 |
|
〉 |