

Journal of Geo-information Science >
Blind Watermarking Algorithm Based on Normalization for Vector Data
Received date: 2014-10-29
Request revised date: 2014-11-24
Online published: 2015-07-08
Copyright
In vector data watermarking technology, the geometric transform attack is commonly difficult to cope with. The existing algorithms that can resist the attacks of geometric transformation, however always cannot resist vertexes attacks. Therefore, a blind watermarking algorithm for vector data is proposed based on the idea of data normalization to solve this problem. In this algorithm, the coordinate values of spatial data were normalized before embedding the watermarks, in order to keep invariant with respect to translation and zooming. Watermarks were embedded in the normalized values of the vertex coordinate data for several times. There are no original data needed in the procedure of watermark detecting. The experiments show that the algorithm is robust against a series of different attacks, such as translation or scaling transformations, vertex insertion and removal, cropping, compression, reordering and data format conversion. In addition, it can control and limit the relevant errors of the watermarked spatial data that produced during the watermark embedding.
Key words: normalization; vector data; robustness; blind watermarking
ZHANG Liming , YAN Haowen , QI Jianxun , ZHANG Yongzhong . Blind Watermarking Algorithm Based on Normalization for Vector Data[J]. Journal of Geo-information Science, 2015 , 17(7) : 816 -821 . DOI: 10.3724/SP.J.1047.2015.00816
Fig. 1 Watermarks embedding flowchart图1 水印嵌入流程图 |
Fig. 2 Watermarks detecting procedure图2 水印提取过程 |
Fig. 3 Original watermark图3 原始水印 |
Tab. 1 Relationship between maximum error, RMSE and n表1 n值与最大误差、RMSE关系 |
| n | MaxError | RMSE | NC |
|---|---|---|---|
| 3 | 0.218261585 | 0.030237424 | 0.817871 |
| 4 | 0.021826158 | 0.003048796 | 0.821289 |
| 5 | 0.002182616 | 0.000304115 | 0.833008 |
| 6 | 0.000218262 | 3.04633E-05 | 0.843008 |
| 7 | 2.18262E-05 | 3.02807E-06 | 1 |
| 8 | 2.18262E-06 | 3.03757E-07 | 1 |
| 9 | 2.18262E-07 | 3.03369E-08 | 1 |
| 10 | 2.18262E-08 | 3.01902E-09 | 1 |
| 11 | 2.18262E-09 | 3.02866E-10 | 1 |
| 12 | 7.74349E-11 | 8.3593E-12 | 1 |
| 13 | 2.18304E-11 | 3.0356E-12 | 1 |
| 14 | 2.1892E-12 | 3.036E-13 | 1 |
| 15 | 2.174E-13 | 3.03E-14 | 0.999512 |
| 16 | 2.93E-14 | 3E-15 | 0.749023 |
Fig. 4 Error distribution histograms图4 误差分布直方图 |
Fig. 5 Visualization comparison图5 可视化比较 |
Tab. 2 Robustness for geometric attacks表2 几何攻击的鲁棒性 |
| 攻击类型 | 平移5 | 放大2倍 | 缩小0.5倍 |
|---|---|---|---|
| 水印 | 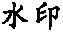 | 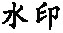 | 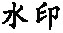 |
| NC | 1 | 1 | 1 |
Tab. 3 Robustness for vertex insertion, removal and modification attacks表3 増、删点及修改点攻击的鲁棒性 |
| 攻击类型 | 点增到24 4260个 | 删除10%点 | 修改10%点 | 修改50%点 |
|---|---|---|---|---|
| 水印 | 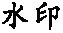 | 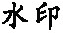 | 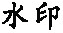 | 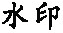 |
| NC | 1 | 1 | 1 | 1 |
Tab. 4 Robustness for compression and removal attacks表4 压缩、要素删除攻击的鲁棒性 |
| 攻击类型 | 阈值0.002坐标点压缩至 41 431个 | 阈值0.02坐标点压缩至 12 903个 | 删除20%要素 | 删除50%要素 |
|---|---|---|---|---|
| 水印 | 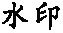 |  | 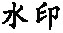 | 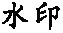 |
| NC | 1 | 0.907715 | 1 | 1 |
Fig. 6 Visualization of data after cropping and the extracted watermark图6 裁剪后数据及提取到的水印 |
The authors have declared that no competing interests exist.
| [1] |
|
| [2] |
|
| [3] |
|
| [4] |
|
| [5] |
|
| [6] |
|
| [7] |
|
| [8] |
|
| [9] |
|
| [10] |
|
| [11] |
|
| [12] |
|
| [13] |
|
| [14] |
|
| [15] |
|
| [16] |
|
| [17] |
|
| [18] |
|
| [19] |
|
| [20] |
|
/
| 〈 |
|
〉 |