

顾及时空邻近的恐怖团伙关系发现方法
|
刘慧敏(1977— ),女,湖南宁乡人,博士,副教授,主要从事时空大数据融合与信息服务研究。E-mail: lhmgis@163.com |
收稿日期: 2020-04-25
要求修回日期: 2020-07-11
网络出版日期: 2021-06-25
基金资助
国家自然科学基金项目(41771492)
湖南省自然科学基金青年基金项目(2018JJ3639)
版权
A Method of Finding the Relationship between Terrorist Groups Considering Spatiotemporal Proximity
Received date: 2020-04-25
Request revised date: 2020-07-11
Online published: 2021-06-25
Supported by
National Natural Science Foundation of China(41771492)
Youth Fund Project of Natural Science Foundation of Hunan Province(2018JJ3639)
Copyright
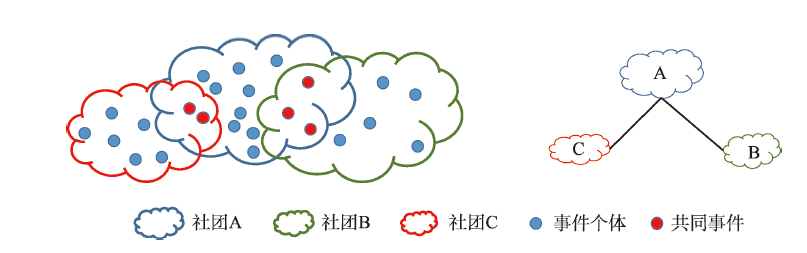
现有恐怖团伙关系挖掘方法因其难以顾及恐怖组织特有的结构复杂、行动灵活、生存期长等特点而难以应用于反恐研究中。为此,本文从时空角度出发,通过引入时空邻近与团伙时空同现模式等概念,将多元独立分布的团伙关系发现问题建模为时空同现模式的频繁度评价问题,提出一种点模式分布下的团伙关系挖掘方法。基于此方法构建团伙关系网络,进而提出一种顾及时空邻近的社团关系度量方法。采用该方法对阿富汗与巴基斯坦地区1970—2018年真实GTD数据进行实验分析,结果表明:该研究区域主要恐怖团伙中共存在11种团伙关系({Taliban,TTP}等),在团伙关系网络中占据核心地位的恐怖组织为Taliban,其次为TTP、BLA。本文提出的方法能有效地挖掘出恐怖团伙之间潜在的关系,团伙关系的定量表达度量了不同组织在关系网络中的地位,验证分析表明,挖掘结果与相应团伙共同参与事件的时空分布、历史根源高度吻合。本文拓展了时空同现模式挖掘在恐怖团伙关系发现中的应用,研究成果对公安部门在识别某些恐怖事件制造者以及合理分配警力资源方面具有重要意义。
刘慧敏 , 刘青豪 , 陈袁芳 , 石岩 , 邓敏 . 顾及时空邻近的恐怖团伙关系发现方法[J]. 地球信息科学学报, 2021 , 23(4) : 584 -592 . DOI: 10.12082/dqxxkx.2021.200199
The existing methods of mining the relationship between terrorist groups are difficult to be applied in anti-terrorism researches because of the unique characteristics of terrorist group relationship such as complex structure, flexible action, and long survival period. From the perspective of time and space, based on the characteristics of spatiotemporal proximity and spatiotemporal co-occurrence of terrorist groups, the relationship of multiple independently distributed terrorist groups is modeled as the frequency of spatiotemporal co-occurrence in our study. We propose a method of terrorist group relationship mining based on the distribution of point mode. Based on this method, a terrorist group network can be constructed. We further applied this method to analyze the real GTD data of Afghanistan and Pakistan from 1970 to 2018. The results show that there are mainly 11 types ({Taliban,TTP}, etc.) of terrorist group relationship in our study area. The terrorist organization that occupy the core position in the network is Taliban, followed by TTP and BLA. The method proposed in this study can effectively quantify the potential relationship between terrorist groups. The quantified terrorist group relationship also indicates the positions of different organizations in the network. Our verification analysis shows that our results are highly consistent with the spatiotemporal distribution and historical roots of the terrorist events. This study expands the application of spatiotemporal co-occurrence pattern in discovering the relationship of terrorist groups. Our results are of great significance to the public security department in identifying the perpetrators of certain terrorist incidents and reasonably allocating police resources.

表1 团伙时空同现模式挖掘结果Tab. 1 Mining results of temporal and spatial co-occurrence patterns of gangs |
| 团伙时空同现模式 | 同现实例组合数/个 | 同现频繁度 |
|---|---|---|
| {Taliban,TTP} | 1489 | [0.183, 0.609] |
| {Taliban,KCIS} | 1027 | [0.123, 0.875] |
| {TTP, KCIS} | 126 | [0.109, 0.335] |
| {TTP, LeI} | 69 | [0.086, 0.679] |
| {BRA,BLA} | 48 | [0.169, 0.206] |
| {BRA,UBA} | 35 | [0.103, 0.220] |
| {BLA,LeJ} | 21 | [0.119, 0.177] |
| {BLA,UBA} | 32 | [0.119, 0.305] |
| {LeJ, UBA} | 8 | [0.071, 0.073] |
| {Taliban,TTP,KCIS} | 330 | [0.030, 0.095, 0.290] |
| {BLA, LeJ, UBA} | 12 | [0.097, 0.047, 0.061] |
表2 GTD数据中恐怖团伙合作事件统计Tab. 2 Statistics of terrorist group cooperation events in GTD data |
| 主要参与团伙 | 事件数量/件 | 部分GTD事件编号 |
|---|---|---|
| {Taliban, TTP} | 11 | 201405120079, 201407050055, 201407310012, 201412140015, 201605180065, 201605180066… |
| {Taliban, KCIS} | 34 | 201503240037, 201511210004, 201601310004, 201606050047, 201606200015, 201606200016… |
| {TTP, KCIS} | 20 | 201601130006, 201602120004, 201605120032, 201605180017, 201605180018, 201605250025… |
| [1] |
马愿. 《2018年全球恐怖主义指数报告》解读[J]. 国际研究参考, 2019(2):38-42,56.
[
|
| [2] |
https://www.start.umd.edu/gtd/.
|
| [3] |
富育红. 阿富汗主要反叛团伙及其关联[J]. 南亚研究季刊, 2015(1):30-38.
[
|
| [4] |
康树华. 有组织犯罪的特征与分类[J]. 南通师范学院学报(哲学社会科学版), 2004,20(3):33-41.
[
|
| [5] |
王钢, 刘猜. 犯罪团伙网络关系模型及分析方法[J]. 中国人民公安大学学报(社会科学版), 2015,31(3):61-71.
[
|
| [6] |
张兵. 关系、网络与知识流动[M]. 北京: 中国社会科学出版社, 2014.
[
|
| [7] |
|
| [8] |
|
| [9] |
付举磊, 孙多勇, 肖进, 等. 基于社会网络分析理论的恐怖组织网络研究综述[J]. 系统工程理论与实践, 2013,33(9):2177-2186.
[
|
| [10] |
徐枫, 陈袁芳, 蔡建南, 等. 基于点过程模拟的时空级联模式统计挖掘方法[J]. 中南大学学报(自然科学版), 2017,48(10):2715-2722.
[
|
| [11] |
|
| [12] |
|
| [13] |
李慧, 张南南, 曹卓, 等. 基于机器学习的恐怖分子预测算法[J]. 计算机工程, 2020,46(2):315-320.
[
|
| [14] |
|
| [15] |
位珍珍. 后911时代恐怖主义的GTD数据分析[J]. 情报杂志, 2017,36(7):10-15.
[
|
| [16] |
|
| [17] |
叶文菁, 吴升. 基于加权时空关联规则的公交扒窃犯罪模式识别[J]. 地球信息科学学报, 2014,16(4):537-544.
[
|
| [18] |
|
| [19] |
李智, 李卫红. 点模式条件下的犯罪嫌疑人时空同现模式挖掘与分析[J]. 地球信息科学学报, 2018,20(6):827-836.
[
|
| [20] |
赵国军. “东突”恐怖活动常态化及其治理[J]. 国际展望, 2015,7(1):104-117, 156-157.
[
|
| [21] |
|
| [22] |
袁沙. 巴基斯坦国内恐怖主义势力的演变、特点及影响分析[J]. 南亚研究季刊, 2016(2):33-41,5.
[
|
/
| 〈 |
|
〉 |